
Enterprise Iot
Article | July 20, 2023
Explore the world of readings on IoT security, to address complex cyber security challenges and privacy issues. It caters to a wide range of readers including industrialists, students & enthusiasts.
The Internet of Things (IoT) has revolutionized industries, enabling innovative applications and improved efficiency. However, along with the numerous benefits of the IoT comes the pressing need for robust security measures. As IoT devices become more prevalent and interconnected, their risks and vulnerabilities also increase. The experts in the domain must stay updated with the latest security practices and techniques to ensure IoT systems' integrity, confidentiality, and availability. A wide range of books has been explicitly tailored address these security concerns.
1. Analytics for the Internet of Things (IoT)
Author: Andrew Minteer
Analytics for the Internet of Things (IoT): Intelligent analytics for your intelligent devices provides a comprehensive guide for businesses aiming to make informed decisions and gain greater control over their IoT infrastructure. Written by an expert in the field, this book equips readers with the essential knowledge and techniques to solve the unique challenges associated with IoT and extract valuable insights from vast amounts of data. The book begins by tackling the complex task of extracting value from large volumes of often complex IoT data, empowering readers to make data-driven decisions. Strategies to address data quality concerns are discussed, ensuring that readers are equipped to handle the inherent challenges. It offers readers approaches to optimize business value and bring down costs. Scaling both data storage and analytics is a critical consideration in IoT deployments, and the book provides practical insights into handling scale effectively. The book covers a range of topics, including transmission protocols, data flow, value extraction, geospatial analytics, machine learning, and optimizing business value.
2. Industrial Internet of Things (IIoT)
Editors: R. Anandan, Suseendran Gopalakrishnan, Souvik Pal, Noor Zaman
One of the essential IoT security books, Industrial Internet of Things (IIoT): Intelligent Analytics for Predictive Maintenance comprehensively explores how the industrial internet is transforming through increased network agility and the ability to deploy, automate, integrate artificial intelligence, orchestrate, and secure diverse use cases at hyperscale. The adoption of industrial automation on a large scale is revolutionizing business processes, with the market for industrial robots projected to reach $73.5 billion by 2023. The book highlights how IoT industrial automation provides numerous advantages, including enhanced efficiency, high accuracy, cost-effectiveness among others. This book presents real-world case studies in IIoT, robotic and intelligent systems, and web-based applications. The content is tailored to appeal to a broad audience, including working professionals, educators, and researchers in various technical disciplines. The book provides industry leaders with valuable insights by proposing business models that revitalize the workforce.
3. IoT and OT Security Handbook
Authors: Smita Jain, Vasantha Lakshmi, Foreword: Dr Rohini Srivathsa
IoT and OT Security Handbook: Assess risks, manage vulnerabilities, and monitor threats with Microsoft Defender for IoT is a comprehensive guide that equips industrial security, IoT security, and IT security professionals with the knowledge and tools to effectively address cybersecurity challenges in the rapidly evolving world of IoT and OT. In the era of the Fourth Industrial Revolution, where digital transformation and connected industries dominate, the book sheds light on the pressing security concerns that must be addressed to ensure data protection and operational resilience. Through a deep dive into the Purdue model of reference architecture, readers gain a solid understanding of common cyber-attacks prevalent in IoT and OT environments. The centerpiece of the book revolves around Microsoft Defender for IoT, a powerful security solution specifically designed to safeguard IoT and OT ecosystems. Furthermore, the concept of zero trust, which is crucial for establishing a robust security foundation, is thoroughly explored with practical insights on its implementation in the context of IoT devices.
4. Practical Internet of Things Security
Author: Brian Russell, Drew Van Duren
Practical Internet of Things Security: Design a security framework for an Internet connected ecosystem is an indispensable guide that navigates the complex realm of securely building and deploying systems in our IoT-connected world. The book primarily targets IT security professionals, security engineers, and individuals responsible for ensuring the security of their organization's data in the IoT landscape. However, it also serves as a valuable resource for business analysts and managers seeking to understand and address the security challenges associated with IoT deployments. Readers will gain a wealth of knowledge and practical skills, including breaking down cross-industry barriers, building a rock-solid security program, applying systems security engineering and privacy-by-design principles, and harnessing cloud-based systems. It delves into the unique security challenges associated with IoT and provides practical guidelines for architecting and deploying a secure IoT ecosystem within an enterprise.
5. IoT: Security and Privacy Paradigm (Internet of Everything (IoE))
Editors: Souvik Pal, Vicente García Díaz, Dac-Nhuong Le
IoT: Security and Privacy Paradigm is a comprehensive and authoritative resource that explores the evolution of security and privacy issues within the realm of the IoT. This book serves as a single reference point for students, researchers, and practitioners seeking to better understand the IoT security platforms and privacy landscape. The book adopts security engineering and privacy-by-design principles to design and implement robust cyber-security solutions within IoT ecosystems. It takes readers on a journey, starting with exploring security issues in IoT-enabled technologies and their practical applications. The book provides practical guidance on tackling security challenges and constructing a secure infrastructure for IoT devices. The book thoroughly discusses security challenges and solutions in areas such as RFID, WSNs, and IoT. The primary audience for this book includes specialists, researchers, graduate students, designers, experts, and engineers focused on security-related issues and research.
6. IoT Security Issues
Author: Alasdair Gilchrist
IoT Security Issues addresses the rapid proliferation of internet-connected devices, where security often takes a backseat to product development. This book delves into the inherent vulnerabilities and IoT security challenges, offering insights on how to address and mitigate these issues. By examining the root causes of these problems and emphasizing the importance of programming and security best practices, the author presents practical solutions to combat the lax security processes prevalent in the IoT landscape. This book caters to a wide range of readers, including programmers who have yet to focus on the IoT, security professionals, and individuals with a keen interest in hacking and making. While a basic programming background would be beneficial for certain chapters later in the book, the core content is explained in a manner that is approachable for readers from various backgrounds.
7. Security and Privacy Issues in IoT Devices and Sensor Networks
Editors: Sudhir Kumar Sharma, Bharat Bhushan, Narayan C. Debnath
This book, of all the IoT security books, delves into the critical aspects of security breaches in IoT and sensor networks, offering a comprehensive exploration of potential solutions. The book takes a two-fold approach, thoroughly examining the fundamentals and theoretical foundations of sensor networks and IoT security. It then explores the practical IoT security solutions that can be implemented to enhance the security of these elements, providing illuminating case studies to reinforce understanding. The book is an invaluable resource for industry professionals working with wireless sensor networks (WSN) and IoT systems, enabling them to elevate the security of these interconnected systems. Additionally, researchers, material developers, and technology specialists grappling with the intricate nuances of data privacy and security enhancement will find the book's comprehensive information highly beneficial.
Final thoughts
IoT security for professionals involves implementing secure communication protocols, strong authentication, device management, data encryption, access control, and regular security audits. It is crucial to stay updated, maintain a security-aware culture, and prioritize the ongoing monitoring and adaptation of security measures to address emerging threats.
The above listed books delve into various aspects of IoT security, providing insights, strategies, and practical solutions to mitigate risks and protect IoT ecosystems. This article highlights some essential IoT security books that are indispensable resources for IoT professionals striving to enhance the security posture of their organizations. They also provide real world case studies, best practices and strategies to minimize risks.
Read More

Enterprise Iot
Article | May 11, 2023
Explore the IoT certifications and grow your skills with the transforming landscape. Including Iot security certifications, this curated list will help you to boost career in the IoT industry.
As the Internet of Things continues to expand its reach across industries, the need for robust security measures to safeguard connected devices and data has become paramount. With IoT systems' growing complexity and interconnectivity, organizations seek professionals with specialized knowledge and expertise in IoT security. In response to this demand, various certifications have emerged to validate individuals' skills and provide them with a competitive edge in the IoT industry. In this article, we will explore some key IoT security certifications that can significantly enhance one's career prospects and contribute to IoT solutions' safe and secure deployment.
1. IoT Security Certification and Cybersecurity
Intertek’s IoT Security Certification and Cybersecurity provides IoT certification and testing services to validate the security of connected products. Securing endpoints and ecosystems has become crucial with the rapid growth of the Internet of Things. Intertek's total quality assurance approach involves understanding the product, use cases, integration with other systems, and developing a roadmap to ensure compliance with industry standards and regulations. Their IoT security and cybersecurity experts guide clients in choosing the most relevant program for their product and target markets, instilling confidence in product security. Intertek offers services such as the Cyber Assured Program, vulnerability assessments, penetration testing, testing to standards like ANSI/UL 2900 and IEC 62443, connected medical device security, industrial automated control systems security (IEC 62443), and advisory services. Intertek's expertise helps clients address cybersecurity risks and ensure the security of their IoT products.
2. Securing IoT - Build secure IoT solutions: 2-in-1
The Securing IoT: Build Secure IoT Solutions: 2-in-1 course is a comprehensive training program designed to help IoT product designers, IoT product managers, IT security professionals, and security engineers build secure and robust Internet of Things systems. The course consists of 'Fundamentals of IoT Security' and 'Security Engineering for the IoT.' The learners will delve into IoT security architectures, regulations, and standards. Privacy concerns and Privacy by Design principles and practical examples of conducting Privacy Impact Assessments are addressed. Cryptographic solutions, identity and access management, and key management solutions are explored, along with the cloud's secure connectivity, processing, and storage of data. By the end of the program, participants will have the skills to identify threats to their organization's data and IoT systems, employing design techniques, applied cryptography, and secure cloud connectivity for robust security.
3. IOT Security Professional (ICIP)
The IoT Security Professional (ICIP) program offered by ISAC is designed to provide participants with a comprehensive understanding of cyberattacks on IoT and SCADA systems. The training focuses on offensive testing techniques to better understand and combat hack and malware attacks. Participants will learn about discovering sensitive devices, network hacking via IoT, hacking smart devices, and controlling SCADA systems. The program includes case studies on malware like WannaCry and Crash Override and defensive measures like threat intelligence and endpoint protection. The course suits security researchers, forensic investigators, security teams, law enforcement agencies, and military personnel. Successful completion of the program grants a Clean Exit Professional Ethics Certification and inclusion in the National Security Database.
4. Internet of Things Security Expert Training
The Internet of Things Security Expert course offered by Cognixia is a comprehensive training program designed for professionals seeking to enhance their knowledge of IoT security. The course covers various IoT security platforms and provides hands-on training with relevant tools. It consists of three major modules: python, advanced IoT training and certification, and IoT Security. The Python module familiarizes candidates with the versatile programming language and its applications in IoT development. The Advanced IoT Training and Certification module covers IoT ecosystems' architecture, development, deployment, and security with real-life case studies. The IoT Security module focuses on securing IoT devices, covering architecture, practical attacks, vulnerability disclosure, and securing connected products. The course offers lifetime access to learning materials and round-the-clock technical support.
5. IOT Analyst Certification
One of the online IoT certification courses, the IT Analyst Certification is a 12-month program that focuses on combining IoT with Analytics to unlock valuable data from connected IoT devices. The course comprises three courses covering data acquisition, exploratory analysis, cleaning, and final analysis for IoT systems. It also teaches how advanced analytics and machine learning algorithms can be applied to build complex IoT solutions. The program is suitable for students from all backgrounds, and no prior knowledge of analytics or IoT is required, although basic quantitative skills are beneficial. After completing the curriculum and passing the certification test, students receive the IOT Analyst Certification, enabling them to process and analyze data from IoT sensors and become proficient in IoT analytics. The certification opens up opportunities in the fast-growing Big Data and Analytics industry, where IoT analytics is widely applied to predict future technology trends.
6. IOT Professional Certification
The IOT Professional Certification offered by Jigsaw Academy is a comprehensive program designed to help individuals master the implementation of IoT using Arduino. This 12-month online iot certification course uses the Arduino platform to build IoT solutions from scratch. The program consists of four courses covering various IoT aspects, including sensor-connected devices and gateways. Students will engage in hands-on exercises, real-life case studies, and a capstone project to apply their knowledge effectively. Upon completion, students receive a certification that validates their skills in building and applying IoT solutions, setting up IoT Cloud for data storage and analysis, and proficiency in Arduino programming language. The IOT Professional Certification equips individuals with the necessary skills and knowledge to excel in the high-demand field of IoT and opens up better job prospects.
7. IoT and its Applications
TCS iON Digital Learning Hub offers the 'IoT and its Applications' certificate course, providing learners with a comprehensive understanding of the fundamentals of the Internet of Things. The course spans 5 to 6 months, delivered in English through digital lectures, e-learning resources, and community-based virtual classrooms. Through industry assignments and expert-led instruction, participants gain theoretical and practical insights into IoT applications. Upon completion, learners receive a verifiable digital certificate and gain industry-level skills required for test engineers or computer programmers. This course helps learners grasp IoT theories and practical applications, offering valuable career opportunities.
Conclusion
In an era where the Internet of Things is transforming industries and revolutionizing the way, we interact with technology, ensuring the security of IoT systems has become a critical imperative. The certifications discussed in this article represent a selection of key credentials available to professionals seeking to boost their careers in the IoT industry. By obtaining these certifications, individuals can validate their expertise in IoT security, demonstrating their commitment to upholding best practices and safeguarding the integrity of connected devices and data.
As the demand for IoT security professionals continues to rise, these certifications will serve as powerful assets, opening doors to exciting opportunities and positioning individuals as trusted experts in the ever-evolving field of IoT security. By investing in these certifications, professionals can take significant strides toward advancing their careers and contributing to the secure and responsible growth of the IoT ecosystem.
Read More
IoT Security
Article | July 17, 2023
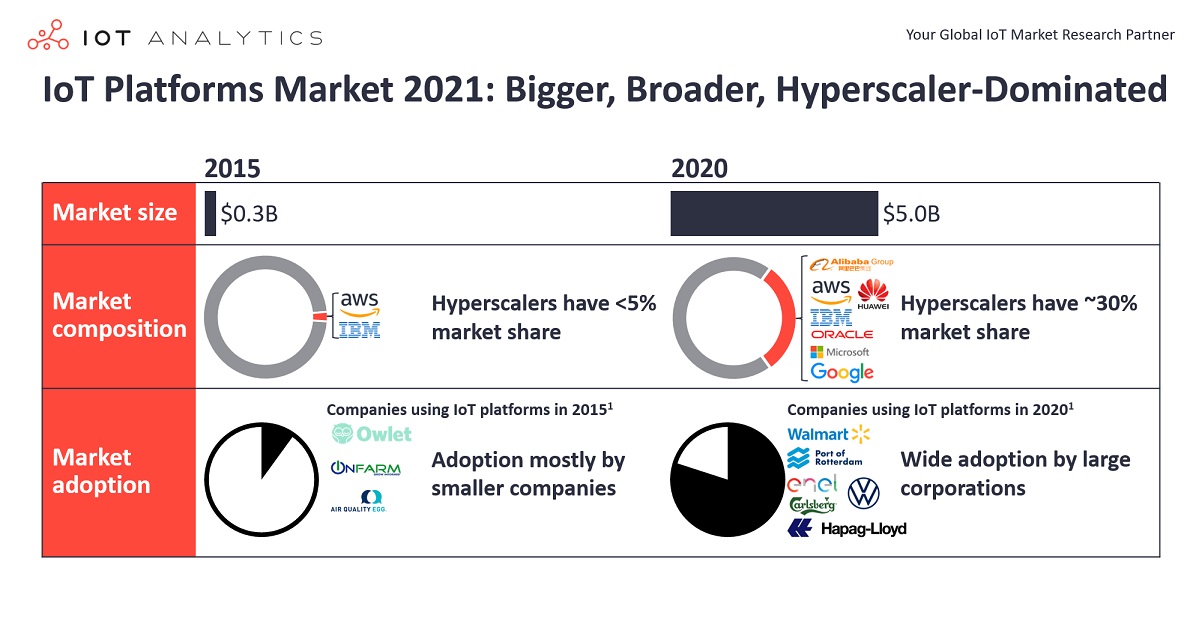
5 years ago, when we forecasted that the IoT platforms market would have a 5-year compound annual growth rate (CAGR) of 35%, we wondered if our growth projection was unrealistically high.
5 years later, it has become apparent that the forecast was actually too low. The IoT Platforms market between 2015 and 2020 grew to be $800 million larger than we forecasted back in early 2016, resulting in a staggering 48% CAGR.
Comparing what we “knew” back in 2016 to what we know today provides some clues as to why the market exceeded expectations so much. 5 years ago, no one really knew what an IoT platform was, let alone how big the market would be, which business models would work, how architectures would evolve, and which companies/industries would adopt them. The only thing that was “known” was that the IoT platforms market was a billion dollar “blue ocean” opportunity ready to be captured by innovative companies.
Read More
Industrial IoT, IoT Security
Article | July 11, 2023
Explore the IoT tools for security and maintenance. These IoT monitoring tools addresses cyber security and privacy issues, catering to a various users including industrialists & individuals.
With the proliferation of interconnected devices in the Internet of Things ecosystem, ensuring robust security measures has become crucial to protect against cyber threats. The complexity and diversity of IoT systems pose unique challenges, making thorough security testing an essential practice. To address these challenges, various IoT development tools have emerged that enable organizations to assess and mitigate vulnerabilities in their IoT deployments. In this article, explore the top ten tools to secure IoT and IoT testing, equipping professionals and organizations with the means to identify and address potential security weaknesses, thus bolstering the overall security posture of their IoT infrastructure.
1. AWS IoT Device Defender
AWS IoT Device Defender is one of the security IoT management tools, designed to protect and manage IoT devices and fleets. Its auditing capabilities and continuous monitoring enable users to assess their IoT resources' security posture, identify vulnerabilities, and address potential gaps. By leveraging machine learning models or defining custom device behaviors, it can monitor and detect malicious activities, such as traffic from suspicious IP addresses or unusual connection attempts. The tool provides security alerts for failed audits or behavior anomalies, allowing users to mitigate potential risks quickly. Built-in actions facilitate security issue resolution, including device certificate updates, quarantine, and policy replacements. AWS IoT Device Defender offers automation for security assessments, identification of attack vectors, analysis of historical device behavior, and alarm notifications through various AWS interfaces.
2. Dynamic Application Security Testing
Appknox offers two robust mobile application security solutions: Automated Dynamic Application Security Testing (DAST) and Penetration Testing (PT). With Automated DAST, users can assess the security of their mobile apps in real time while running in their operational environment. The solution provides access to real devices, allowing users to replicate real-life interactions and identify security vulnerabilities. On the other hand, Appknox's Penetration Testing solution delivers reliable and thorough security assessments by expert security researchers. Users can request a manual pentest effortlessly, and the skilled team analyzes apps to identify and eliminate potential threats. The process includes identifying the tech stack, analyzing the threat landscape, setting up breakpoints, testing responses, detecting bugs, and performing advanced threat exploits.
3. Enterprise IoT Security
Enterprise IoT Security is a comprehensive Zero Trust solution designed to address IoT devices' security challenges in modern enterprises. It helps eliminate implicit trust and enforces zero-trust principles through least privilege access, continuous trust verification, and continuous security inspection. With this solution, organizations can quickly discover and assess every IoT device, easily segment and enforce the least privileged access, and protect against known and unknown threats. By simplifying operations, Enterprise IoT Security enables faster deployment, with a 15-time faster deployment than other solutions. The solution offers better and faster protection for IoT devices, delivering 70 times more security efficiency and 20 times speedier policy creation.
4. Azure Sphere
Azure Sphere is a secure IoT platform offered by Microsoft that allows businesses to create, connect, and maintain intelligent IoT devices. It provides end-to-end security, from the silicon level to the operating system (OS) to the cloud. With Azure Sphere, organizations can securely connect, manage, and protect existing and new IoT devices. The platform offers over-the-air updates, integration with IoT platform services, and continuous security improvements. It helps businesses deploy real-time security patches, maintain device operations, and accelerate time to market. Azure Sphere incorporates essential security properties and offers comprehensive security and compliance.
5. Microsoft Defender for IoT
Microsoft Defender for IoT is a comprehensive security solution that provides real-time asset discovery, vulnerability management, and threat protection for the Internet of Things and industrial infrastructure, including ICS/OT environments. It offers context-aware visibility into IoT and OT assets, enabling organizations to manage their security posture and reduce attack surfaces based on risk prioritization. With behavioral analytics, it detects and responds to attacks across IT and OT networks. Integrated with SIEM/SOAR and XDR tools, it delivers unified security and leverages threat intelligence for automatic response. Microsoft Defender for IoT is designed to meet the unique security needs of various industries and supports complete endpoint protection when combined with Defender for Endpoint.
6. IoT Security
Forescout offers an IoT security solution that automates security measures and provides visibility for every device connected to the network. Their zero-trust approach ensures complete device visibility, proactive network segmentation, and least-privilege access control for IoT, OT, IoMT, and IT devices. The platform classifies and monitors devices in real time, identifies weak credentials, and enforces strong passwords. It also enables dynamic network segmentation and automates zero trust policy orchestration across multi-vendor environments. Forescout's solution efficiently manages asset inventory and device lifecycle and has been proven to scale for enterprise-level deployments.
7. ThingSpace
The ThingSpace Platform for IoT offers a comprehensive set of iot tools and devices for developing and managing the lifecycle of IoT devices. It enables connectivity management at scale, allowing secure activation on the Verizon network and providing features to troubleshoot, locate, and manage IoT devices. Whether at the prototype stage or ready to scale for enterprise-level deployment, ThingSpace provides the necessary resources for IoT solution development and management. As a Magic Quadrant Leader for IoT Connectivity Services, ThingSpace offers solutions for software management, device readiness, and overall device lifecycle management. Businesses can collaborate with technology leaders through their Executive Briefing Program to achieve their specific goals and gain a competitive edge.
8. Verimatrix
The Verimatrix Secure Delivery Platform offers a unified user experience by combining cybersecurity and anti-piracy services into a comprehensive cloud ecosystem. It provides media companies, content owners, streaming providers, and broadcast operators with a single pane of glass experience for securing content, applications, and devices. Key offerings include Streamkeeper Multi-DRM for cloud-based digital rights management, Verimatrix App Shield for zero code hardening of mobile applications, Verimatrix Video Content Authority System (VCAS) for real-time monitoring, and Streamkeeper Counterspy for cybersecurity and anti-piracy solutions. The platform also facilitates partner integrations, enabling seamless onboarding and revenue preservation.
9. Trustwave
Trustwave's Managed IoT Security provides comprehensive solutions to secure the Internet of Things (IoT) and minimize the risk of compromise. With expertise from Trustwave SpiderLabs, it offers knowledge about network assets, identifies weaknesses in applications, servers, APIs, and cloud clusters, and enables secure IoT deployment with quick validation of fixes. This reduces the risk of compromised devices, which can lead to various threats, including DoS attacks, privacy violations, and data theft. Trustwave's services cater to IoT developers/manufacturers, offering product security reviews, testing, and incident readiness services. For IoT implementers, it provides managed security services and testing to safeguard deployments and associated data.
10. ARMIS Agentless Device Security Platform
The ARMIS Agentless Device Security Platform supports implementing the Critical Security Controls(CIS) framework. Developed by the Center for Internet Security (CIS), these controls are periodically updated by a global community of experts. ARMIS aligns with the CIS Controls and provides a comprehensive set of security controls to address the framework's requirements. The platform caters to enterprises of all sizes and offers different implementation groups based on risk profile and available resources. With ARMIS, organizations can enhance their cybersecurity posture and implement the CIS Controls effectively.
Final Thoughts
Security is a major concern in IoT tools and software due to the proliferation of connected devices, the diverse and complex nature of IoT ecosystems, the need to protect data privacy and confidentiality, the lack of standardization, the long lifecycles of devices, and the distributed and scalable nature of IoT deployments. Addressing these concerns is crucial to prevent unauthorized access, data breaches, and ensure the integrity and privacy of IoT data.
The IoT tools and technologies discussed in this article represent some of the top options for conducting comprehensive IoT security testing. By leveraging these tools, professionals and organizations can proactively identify and address vulnerabilities in their IoT systems, ensuring their data and devices' confidentiality, integrity, and availability. By incorporating these tools into their security practices, organizations can bolster their IoT security strategy and enhance their ability to protect against emerging threats in the dynamic IoT landscape.
Read More